Installing the Application Server
File
IZYTRON.IQ BackEnd ApplicationServer.msi
Description
This setup installs the application server to IIS.
MSI Package
The MSI package includes the following optional parameters, for which the respectively used default values are specified below. These are used automatically if the corresponding parameter isn’t specifically configured during installation.
INSTALLWEBAPPDIR=<standard wwwroot directory from IIS, usually = c:\inetpub\wwwroot\IZYTRON.IQ>
WEBSITE_NAME = Default Website
WEBAPP_NAME=IZYTRON.IQ
APPPOOL_NAME=IZYTRON.IQ.BackEnd Pool
APPPOOL_USERNAME=ApplicationPoolIdentity
APPPOOL_USERPWD=<password>
With the default settings, the application server is installed as follows:
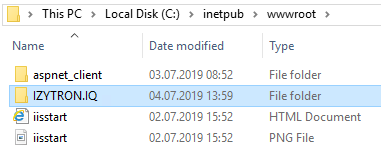
This installs the application server to IIS under “MyWebSite\MyWebApp” (virtual directory) and physically to “c:\myinstalldir”. The application pool (IZYTRON.IQ.BackEnd Pool) (default) is set up with username “myapppooluser” and password “mypwd”, and is assigned to the website.
Alternatively, the user can also be defined via the ApplicationPool in the IIS manager:
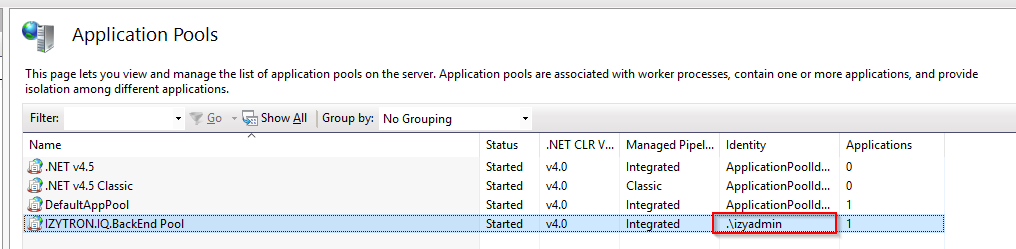
Comments
– The application’s URL is laid out as follows:
https://<certificate path>/<application name>
The certificate path is the path which is specified in the general information for the certificate in IIS: (“General” tab, issued to: <certificate path> in the “Certificate” window).
– If “IZYTRON.IQ BackEnd ApplicationServer.msi” is executed directly by double-clicking, the application server is installed as “Default Web Site\IZYTRONIQ” with the “IZYTRON.IQ.BackEnd Pool” app pool and the following default app pool credentials: ApplicationPoolIdentity.
This user (ApplicationPool) probably doesn’t have any access to the database. A suitable user must be entered to this end (in the app pool’s “Advanced Settings” under “Identity”).
– The following URL can be opened in the browser in order to display the correct installation:
“https://localhost/IZYTRON.IQ/HandshakeRemoteService.svc” (if installed in this way).
In the event of correct installation, an information page is displayed.
https://<certificate path>/IZYTRON.IQ/HandshakeRemoteService.svc
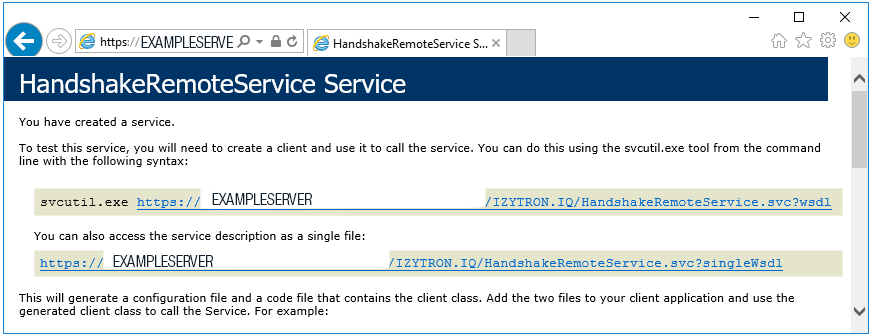
If the page is not displayed, a standard IIS error message appears instead, which provides information concerning any possible installation errors.
– The application uses default HTTPS port 443. The TCP port setting may not be changed.
– A valid certificate must be assigned to the page. Otherwise, the clients are unable to access the application server.
A corresponding binding with a certificate for this purpose must therefore be set up on the
IZYTRONIQ backend server. When installing the
IZYTRONIQ backend application service with the default parameters specified above, binding to the default website must take place in IIS (internet information services). See
„Embedding an SSL Certificate“ for details.

In the Web.Config file, “serviceCertificate” must also be adapted for the tag’s lines (<serviceCertificate> findvalue=“localhost” x509FindType=“FindBySubjectName” storeLocation=“LocalMachine” storeName=“My”):
– The value for “findValue” must be set to the certificate’s fingerprint or thumbprint here. As shown in the figure above, the fingerprint or thumbprint can be taken from the certificate’s details, which in turn can be found in IIS under Server Certificates.
Enter the fingerprint in capital letters only without spaces, and without hidden special characters.
– “x509FindType” must be changed to “FindByThumbprint”.
Example: <serviceCertificate findValue="1234567890ABCDEF1234567890" storeLocation="LocalMachine" storeName="My" x509FindType="FindByThumbprint" />








